MapR loopbacknfs POSIX Client
The MapR POSIX Client feature allows app servers, web servers, and other client nodes and
apps to read and write directly to a MapR cluster. Starting with the 4.0.2 release, MapR
provides single-user loopbacknfs licenses that give access to one or more
clusters.
| Linux OS Client | MapR POSIX Client | |
|---|---|---|
| Client OS |
|
|
| Installs On Node Type |
|
|
| Access to Cluster |
|
|
| Supported Interfaces |
|
|
| Connection to File System |
|
|
| Security |
|
|
The Linux OS NFS client must go through an NFS gateway, the link to the gateway is not secured, and transmitted data is not compressed.
The following diagram illustrates how the MapR POSIX client (mapr-loopbacknfs) works, in comparison with the Linux OS NFS client (left).
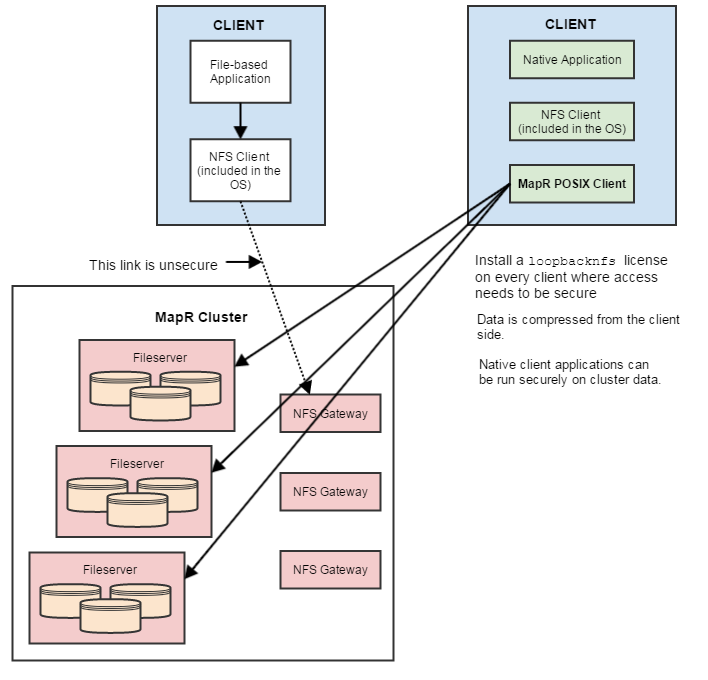
The instructions on this page are for the MapR POSIX client. For instructions on setting up NFS on a MapR cluster, see Setting Up MapR NFS.
| Cluster Security Disabled | Cluster Security Enabled | |
|---|---|---|
| Client Node |
|
|
| Cluster Node |
|
|

